A massive supply chain attack has shaken the crypto ecosystem after hackers compromised widely used JavaScript packages, injecting malware designed to steal digital assets during online transactions. Security researchers have described the incident as the largest supply chain compromise ever recorded, given the billions of weekly downloads affected.
How the Attack Unfolded
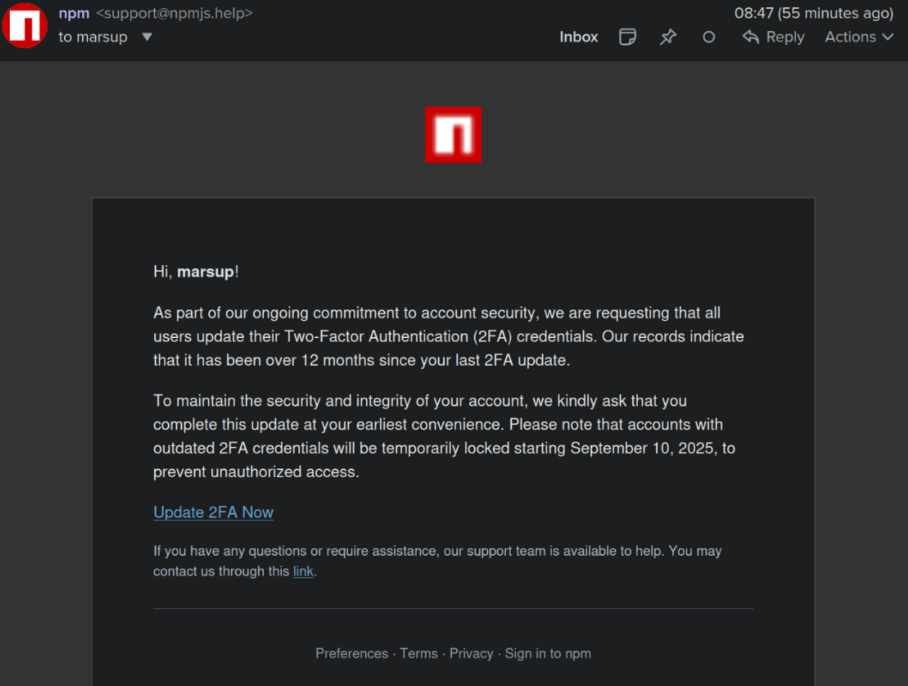
According to BleepingComputer, attackers gained access to NPM package maintainer accounts through phishing emails. The emails, impersonating “support@npmjs.help,” warned developers that their accounts would be locked unless they updated two-factor authentication via a malicious link.
Once maintainers were tricked, hackers injected malware into 18 popular JavaScript libraries, collectively downloaded more than 2.6 billion times each week. Among the compromised tools are some of the ecosystem’s most fundamental packages, including chalk (300 million weekly downloads), debug (358 million), and ansi-styles (371 million).
This widespread infiltration means almost any project relying on JavaScript could be at risk.
Targeting Crypto Transactions
The injected malware is specifically designed to intercept cryptocurrency transfers. Acting as a browser-based interceptor, it monitors network traffic for transactions across major blockchains, including Ethereum, Bitcoin, Solana, Tron, Litecoin, and Bitcoin Cash.
When a user initiates a transfer, the malware silently swaps the destination wallet address for one controlled by attackers, tricking users into sending funds to the wrong account.
Aikido Security researcher Charlie Eriksen explained the severity of the threat:
“What makes it dangerous is that it operates at multiple layers: altering content shown on websites, tampering with API calls, and manipulating what users’ apps believe they are signing.”
This multi-layer manipulation makes the malware extremely difficult to detect.
Hardware Wallets vs Software Wallets
The attack has triggered urgent warnings within the crypto community. Ledger CTO Charles Guillemet stressed that while the malware is highly dangerous, hardware wallets provide a strong line of defence.

Hardware wallet users are protected as long as they carefully verify transaction details before signing. Software wallet users, however, face a much higher risk since they rely on application interfaces that may have already been tampered with.
Guillemet advised:
“If you don’t use a hardware wallet, refrain from making any on-chain transactions for now.”
He added that it is not yet clear whether the attackers can directly extract seed phrases from software wallets, but the risk of address manipulation remains high.
The Scale and Impact
Researchers traced the phishing infrastructure to “websocket-api2.publicvm.com,” highlighting the coordinated nature of the attack. By compromising libraries with billions of weekly downloads, attackers have gained unprecedented reach into cryptocurrency applications and wallet interfaces.
This incident follows a troubling pattern in 2025, with earlier attacks targeting popular JavaScript libraries such as eslint-config-prettier (30 million weekly downloads in July) and multiple NPM packages in March.
While some community members, including pseudonymous DeFi researcher 0xngmi, noted that the effective impact area may be smaller than initially feared, since many projects pin their dependencies or haven’t been updated recently, the scale remains alarming. Users cannot always verify whether a website has upgraded to a compromised package, making precaution essential.
As 0xngmi explained:
“Your wallet is safe and the effective impact area is much smaller than ‘all websites,’ but since you cannot really know if a project pinned dependencies, it’s just safer to avoid using crypto websites till this blows over and they clean up the bad packages.”
The Bigger Picture
The attack demonstrates how fragile modern software supply chains can be. By compromising a handful of trusted packages, hackers managed to infiltrate a global ecosystem used by millions of developers and countless businesses.
For the crypto industry, the incident is a stark reminder that even seemingly indirect vulnerabilities can pose direct risks to digital assets. While hardware wallets remain a strong defense, the attack shows that the surrounding infrastructure: wallet apps, exchanges, and developer tools must also be secured.
As investigations continue, the scale of potential losses remains unclear. But one thing is certain: this supply chain attack has redrawn the threat landscape for both developers and crypto users worldwide.





















































