The Hyper Foundation’s highly anticipated Hypurr NFT airdrop turned sour after blockchain sleuth ZachXBT uncovered a $400,000 exploit. Malicious actors drained eight rare Hypurr NFTs from compromised HyperEVM wallets, flipping them for six-figure profits while legitimate holders were celebrating their windfall.
On Sunday, 28 September, the Hyper Foundation launched its viral collection of cat-inspired NFTs, dubbed “Hypurrs”, to early Hyperliquid adopters. The drop marked one of the most hyped digital asset releases of the year, with secondary market activity reaching record-breaking levels within hours.
Airdrop Turns into Market Sensation
The Foundation had teased the collection since last year’s initial HYPE token distribution, sparking long-standing speculation about its potential impact. That speculation paid off.
Within 24 hours of release, Hypurr NFTs recorded more than 1.3 million HYPE in trading volume, equivalent to over $62 million. At the time of writing, the collection’s floor price hovered around 1,595 HYPE (approx. $76,000), placing Hypurrs firmly among the most valuable NFT drops of 2025.
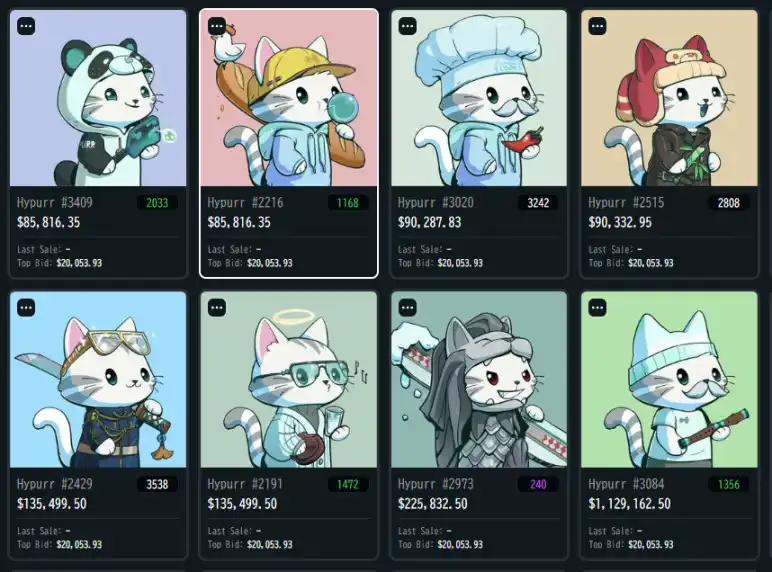
The collection features 4,600 unique feline characters, each boasting distinctive traits. Rarity played a crucial role in driving prices sky-high. Hypurr #21 sold for 9,999 HYPE ($477,000), making it the most expensive to date. Meanwhile, Hypurr #22, one of the rarest in the series with six unique traits, has been listed for an eye-watering 222,700 HYPE ($10.4 million).
ZachXBT Uncovers $400K Exploit
Amid the frenzy, crypto investigator ZachXBT flagged suspicious activity. He traced a malicious HyperEVM address that received and quickly liquidated eight stolen Hypurr NFTs, netting the attacker nearly $400,000.
Unlike Hyperliquid’s off-chain exchange wallets, which do not support NFTs, the Hypurr collection was built on Ethereum’s ERC-721 token standard and deployed via HyperEVM, the chain’s smart contract execution layer.
This design, while enabling advanced features, also opened the door to familiar Ethereum-style vulnerabilities. The stolen NFTs were linked to compromised Externally Owned Accounts (EOAs) on HyperEVM, though the exact method of compromise remains unclear.
Potential Attack Vectors
Security experts note that the attack highlights the risks inherent in hybrid blockchain designs. While Hyperliquid’s bilayered architecture boosts efficiency for perpetual futures trading, HyperEVM introduces classic weaknesses associated with key management.
Possible attack vectors include:
- Phishing scams leading users to sign malicious approvals.
- Compromised private key storage, such as unencrypted files or weak passwords.
- Malware and key loggers targeting users’ devices.
- Malicious smart contracts tricking holders into unsafe interactions.
As of now, the Hyper Foundation has not disclosed details of the breach or recovery efforts.
What It Means for Hyperliquid and NFT Holders
The incident underscores a familiar tension in Web3: innovation comes with attack surfaces. For Hyperliquid, which has positioned itself as a decentralised derivatives powerhouse, the Hypurr exploit raises questions about how its EVM layer balances functionality with security.
For holders, the soaring valuations of Hypurrs demonstrate the collection’s cultural and market appeal, but also highlight the risks of custodying high-value assets in vulnerable wallets.
As the dust settles, all eyes remain on whether the Foundation will move to strengthen wallet security and whether the community will demand more resilient safeguards before Hypurr mania turns into another cautionary tale.

























































