Coinbase has suffered a $300,000 loss in token fees after accidentally granting approval to a 0x Project “swapper” smart contract. The incident, discovered by security researcher Deebeez from Venn Network, allowed a maximal extractable value (MEV) bot to drain funds from the exchange’s corporate wallet.
The issue arose when Coinbase’s corporate fee receiver wallet approved tokens for the swapper contract. While the contract is designed for token swaps, it is permissionless, meaning anyone can trigger it to execute actions, including transferring approved tokens.
Because of this open design, granting token approvals to such a contract exposes funds to immediate theft without needing a code exploit. In this case, an MEV bot had been patiently waiting for such an opportunity and struck immediately.
How the Exploit Happened
According to Deebeez, the swapper contract involved has a history of risky interactions. He highlighted earlier incidents on Zora claims on Base, where a similar setup allowed malicious actors to remove funds simply by using the approved permissions.
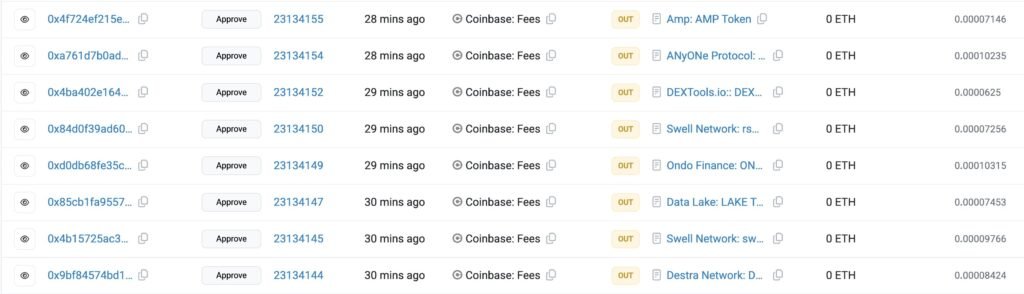
Screenshots posted by the researcher showed that Coinbase approved tokens including:
- Amp (AMP)
- MyOneProtocol (MYONE)
- DEXTools (DEXT)
- Swell Network (SWELL)
Once the approvals were in place, the MEV bot called the swapper contract and drained the wallet of all these tokens, transferring them into its own addresses.
Coinbase’s Response
Coinbase Chief Security Officer Philip Martin confirmed the incident, describing it as an isolated issue linked to a configuration change in one of the company’s corporate decentralised exchange (DEX) wallets.
He stressed that:
- No customer funds were affected.
- Token allowances were immediately revoked.
- Remaining assets were transferred to a new corporate wallet.
While the financial loss is relatively small compared to Coinbase’s overall operations, the incident has been described as an “expensive lesson” in wallet configuration and smart contract approvals.
MEV Bots: Waiting for Mistakes
The attacker in this case was a MEV bot, an automated system designed to profit from blockchain transactions by reordering, inserting or replacing transactions within blocks. In this case, the bot’s “profit” came from an approval mistake rather than exploiting faulty code.
Deebeez noted that the bot had been “lurking in the dark” for some time, waiting for a wallet to mistakenly approve the swapper contract. When Coinbase’s wallet did so, the bot drained it instantly.
This kind of opportunistic attack is not new in the crypto world:
- In April 2024, an MEV bot lost $180,000 in Ether after an attacker exploited its access control and swapped ETH for a worthless token in the same transaction.
- In 2023, a rogue blockchain validator stole $25 million from MEV bots performing “sandwich trades” a form of front-running.
Lessons for the Crypto Industry
This case highlights a key security principle in decentralised finance (DeFi): granting token approvals to permissionless contracts carries significant risk. Once approvals are in place, they can be exploited instantly by anyone with knowledge of the contract’s functions.
For organisations, the incident underscores the need for:
- Careful DEX wallet configuration.
- Rigorous review of contract approvals.
- Continuous monitoring for suspicious allowances.
While Coinbase has assured customers that their funds remain safe, the $300,000 loss serves as a reminder that even major crypto companies are vulnerable to simple but costly mistakes.

























































