The United States Department of Justice has launched a criminal investigation into a former ransomware negotiator accused of secretly taking a cut from crypto ransom payments. The individual, who worked for DigitalMint, a Chicago-based firm specialising in ransomware response was allegedly making secret deals with hackers while helping victims negotiate with them.
DigitalMint confirmed the incident in a statement to Cointelegraph, with company president Marc Grens saying the employee was “immediately terminated” once the suspicious activity came to light. The company is now fully cooperating with law enforcement.
“The investigation involves alleged unauthorized conduct by the employee while employed here,” Grens stated.
“DigitalMint is not a target of the investigation.”
DigitalMint Reacts Quickly to Allegations
DigitalMint has built its reputation on providing secure services to victims of ransomware attacks. The company works with major clients including Fortune 500 companies and is registered with the US Financial Crimes Enforcement Network (FinCEN). It handles crypto transactions for ransomware payments and claims to prioritise security and transparency.
When alerted to the employee’s suspected misconduct, DigitalMint claims it acted swiftly to protect clients and communicate with affected stakeholders.
“Trust is earned every day,” Grens said, adding that the company had taken “immediate action” once the allegations were confirmed.
According to Bloomberg, which first reported the investigation, the unnamed former employee is accused of personally benefiting from deals with hackers, essentially profiting from the same criminals he was supposed to help clients fight.
Trust Issues in the Ransomware Negotiation Industry
The incident has raised concerns about the entire ransomware negotiation industry. While firms like DigitalMint exist to help organisations recover from ransomware attacks, some critics say these companies might not always act in the best interests of their clients.

James Taliento, CEO of cybersecurity company AFTRDRK, told Bloomberg:
“A negotiator is not incentivised to drive the price down or inform the victim of all the facts if the company profits from the ransom amount paid.”
This isn’t the first time such concerns have surfaced. A 2019 investigative report by ProPublica revealed that two other US firms were found to have paid hackers to recover stolen data, while charging their clients extra by pretending they used specialised recovery techniques.
These incidents show the potential for abuse in an industry that often operates in the shadows, with limited oversight and high stakes.
Ransomware Payments on the Decline
Interestingly, the DigitalMint scandal comes at a time when ransomware payments are actually falling. According to cyber response firm Coveware, only 25% of victims paid ransom demands in Q4 of 2024, a significant drop from the 85% who paid in early 2019.
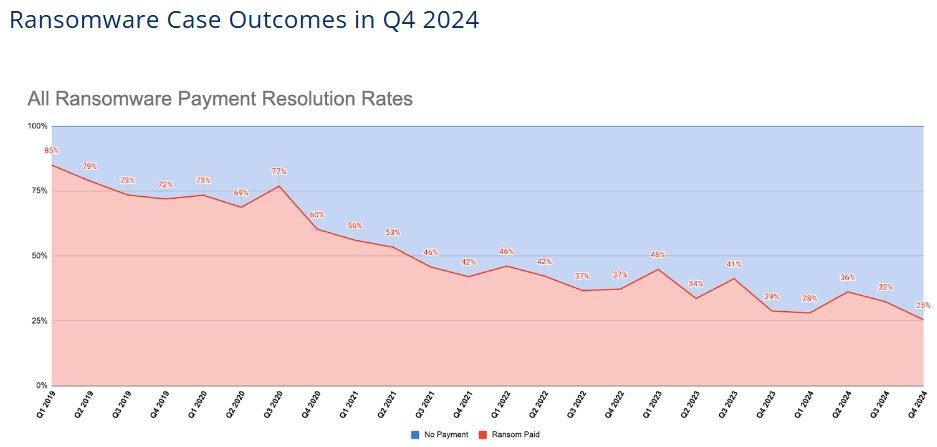
Coveware believes this decline reflects better cybersecurity practices and a stronger willingness among companies to resist extortion. Improved backup and recovery systems, combined with guidance from law enforcement and regulators, have made paying ransoms less appealing.
Meanwhile, the US government continues its crackdown on ransomware gangs. In one of the latest actions, the US Treasury sanctioned Russia-based Aeza Group, a service accused of hosting ransomware and data-stealing tools. Sanctions also targeted top Aeza executives and a connected cryptocurrency wallet.
Additionally, blockchain analytics firm Chainalysis reported that ransomware-related crypto payments fell from $1.25 billion in 2023 to $815 million in 2024.
The investigation into the former DigitalMint employee is a wake-up call for the cybersecurity industry and businesses relying on third-party negotiators. While companies like DigitalMint play a vital role in ransomware response, this case highlights the importance of oversight, transparency, and accountability in an increasingly complex digital crime landscape.
As ransomware attacks evolve, so must the systems in place to combat them — not just in technology, but in ethics and trust.





















































